The word breach indicates that a safeguard has failed and resources that were behind that safeguard are now at risk. Often that threat is virtually, but it can be physical as well.
Currently in the United States, protestors have stormed the United States Capitol and have gained illegal access to offices used by house and senate members. Once the building, or safeguard, was breached the elected officials and staffers were moved to secure areas as they should be.
At this point there is also a threat to the technology infrastructure and data. Now, it could be a random device plugged into an open network jack, or damage to physical technology equipment, or even a breach of the data itself. You would expect measures are in place that would automatically enable screen savers and any systems would be encrypted to limit the risk of access to these machines.
What if that is not the case? A photo posted to social media claiming to be inside Nancy Pelosi’s, the Speaker of the House, office with revolutionaries showing a photo of an unlocked Windows 10 computer.
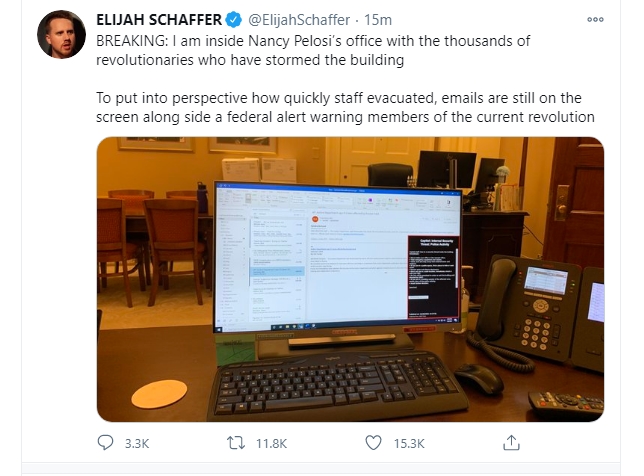
Now your business likely doesn’t contain data similar to that which may be on this specific computer, but what data is on it and how would losing that data or reporting a breach of that data affect your business.
It should be assumed that a data breach has occurred here because the potential of access to confidential files can be validated through the alleged photo.
We should use this as an example to document a plan of action and review the security of your current systems. Which should begin with what is the current screen saver and password requirement policy.
Next you have to assume a data breach occurred so a complete forensic review of systems and network infrastructure has to be completed to validate the data and systems are secure. Every user should be required to change their passwords, and access to technology assets should be blocked until each system is validated.
A review of mailbox rules and analysis of all data leaving the network needs to be blocked and examined to ensure all data leaving is legitimate.
Cyber Attacks and Data Breaches happen multiple ways, when a situation arises that is not normal, it should call us all to use this situation as a learning opportunity and improve our own security.


